Android Security Archive
28 Jan 2012
Android.Counterclank – Another Android Malware
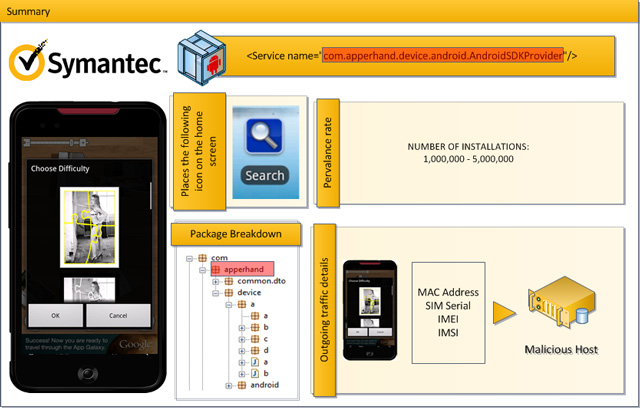
Symantic published the latest list of apps infected by the Android.Counterclank trojan. This trojan can receive commands and can steal information. When an infected app is installed, a malicious service is running with the same name of that of its host app. It is located at the ‘apperhand’ package and another way to know if you are
10 Dec 2011
Avoiding Security Breaches on Your Android Phone

Much has been made in the news recently about malware threat to Android phones. First, it was reported that the Android operating system can be vulnerable to malware threats, largely due to the open nature of its application store. More recently, a study by McAfee Security noted that 2011 will end up being the
20 May 2011
Google is fixing the Android security flaw
A recent discovered security flaw on Android operating system is now being fixed by Google. The recent vulnerability was discovered by German researches that hackers might steal in your information account using rogue-unsecured WiFi connections. I also need to correct my self because there are only three compromised app namely Google Calendar, Contacts and Picasa.
18 May 2011
Android vulnerability – stay away from unsecured hotspots
An Android vulnerability affecting 99% of Android devices has been discovered. The said vulnerability once exploited, hackers can steal your personal information from Facebook accounts, Calendar and other apps if you connect to a rogue WiFi hotspots. Like in computer wireless security Android and other devices such as Blackberries and iOS devices has some soft
04 Mar 2011
How to protect Android against DroidDream malware
With the recent discovery of DroidDream trojan in almost 50 apps and infecting 50K – 200K downloads this is a serious threat. Once the infected app is launched the DroidDream will activate the command and control server and start sending your personal information like IMEI, IMSI, Device Model and SDK version. The known exploit being
03 Mar 2011
Android Market 50 apps discovered to have DroidDream Android Malware
Android is getting popular and becoming a perfect playground for malicious coders. Over 50 apps has been removed from the official Android market after they were discovered to contain malware. The infected apps is said to have the malware dubbed DroidDream. If DroidDream infected app is installed it effectively “rooted” users’ phones and captured personal